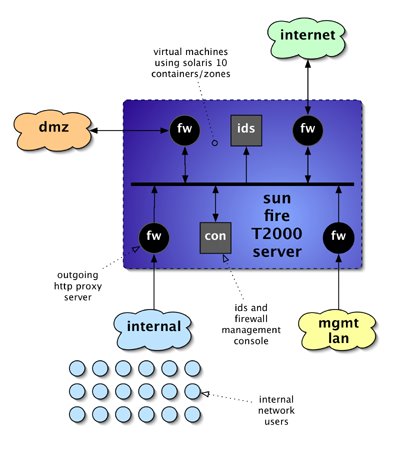
network security appliance diagram
in the above diagram you can see that i intend to virtualise six instances, four firewalls, one ids sensor and a management system. the t2000 has four gigabit ethernet ports, which would be assigned to each of the four networks, while inter-machine communication and intrusion detection would all be done using the virtual internal network. it will be simple to allocate at least one cpu to each machine, and the resource pooling commands available will allow some of the virtual machines to have extra cpus allocated, perhaps the internet-facing firewall and the ids sensor. the sun bigadmin site has some useful resources on zones, including the original usenix paper describing the implementation.
the software to be installed will all be open-source packages, most of which are de-facto industry standards. i will use squid as the outgoing web proxy, snort as the network ids and use native solaris networking for the firewall rules. i will need to determine a suitable console to administer the firewalls, but sguil will be used for ids command and control.
a useful test would be to determine the line-speed that the firewalls and the ids are capable of handling without dropping any packets, and the number of simultaneous outgoing connections that the proxy will allow, while the dmz also has web traffic being sent to it from the internet. i believe that the t2000 should be a good platform for this kind of appliance, due to the one-box approach that can be taken, while not having to compromise on cpu power available. i intend to set this environment up over the next week and produce some performace figures to try and validate this claim.
No comments:
Post a Comment